背景
rtpproxy是rtp媒体代理服务, 支持udp,tcp和webrtc, 和rtpengine功能大体一致。
但是又多了一些功能: 其提供rtp cluster来单独支持rptproxy的集群,
rtpengine没有提供相关的功能。
官方代码地址: rtporxy
官方文档地址: rtpproxy文档
本次测试的rtpproxy版本信息为:
3.1.7456282
安装
安装依赖
本次测试系统版本为:
centos7.9
- gcc > 5.0.0
1
2
3
|
yum install -y devtoolset-10-gcc devtoolset-10-gcc-c++ devtoolset-10-binutils
source /opt/rh/devtoolset-10/enable;
|
- 其他依赖
1
|
yum install -y libsndfile-devel libsndfile libsrtp-devel libsrtp bcg729-devel bcg729
|
安装rtpproxy
1
2
3
|
git clone -b master https://github.com/sippy/rtpproxy.git
git -C rtpproxy submodule update --init --recursive
cd rtpproxy && ./configure && make && make install
|
安装成功之后,可以看到的二进制程序有:
1
2
3
4
5
6
|
[root@localhost rtpproxy]# ll /usr/local/bin/
total 5144
-rwxr-xr-x. 1 root root 122512 Jul 31 03:14 makeann
-rwxr-xr-x. 1 root root 2419936 Jul 31 03:14 rtpproxy
-rwxr-xr-x. 1 root root 2498160 Jul 31 03:14 rtpproxy_debug
-rwxr-xr-x. 1 root root 222032 Jul 31 03:14 udp_contention
|
lib库:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
[root@localhost rtpproxy]# ll /usr/local/lib/rtpproxy/
total 1404
-rwxr-xr-x. 1 root root 948 Jul 31 03:14 rtpp_acct_csv.la
-rwxr-xr-x. 1 root root 137592 Jul 31 03:14 rtpp_acct_csv.so
-rwxr-xr-x. 1 root root 999 Jul 31 03:14 rtpp_acct_csv_debug.la
-rwxr-xr-x. 1 root root 298848 Jul 31 03:14 rtpp_acct_csv_debug.so
-rwxr-xr-x. 1 root root 978 Jul 31 03:14 rtpp_acct_rtcp_hep.la
-rwxr-xr-x. 1 root root 208784 Jul 31 03:14 rtpp_acct_rtcp_hep.so
-rwxr-xr-x. 1 root root 1029 Jul 31 03:14 rtpp_acct_rtcp_hep_debug.la
-rwxr-xr-x. 1 root root 351440 Jul 31 03:14 rtpp_acct_rtcp_hep_debug.so
-rwxr-xr-x. 1 root root 960 Jul 31 03:14 rtpp_catch_dtmf.la
-rwxr-xr-x. 1 root root 124776 Jul 31 03:14 rtpp_catch_dtmf.so
-rwxr-xr-x. 1 root root 1011 Jul 31 03:14 rtpp_catch_dtmf_debug.la
-rwxr-xr-x. 1 root root 286584 Jul 31 03:14 rtpp_catch_dtmf_debug.so
|
实战
运行
1
|
rtpproxy -l 0.0.0.0 -L 4096 -m 40000 -M 40100 -s udp:172.16.4.111:3333 -d DBUG -f -F
|
测试
使用kamailio的rtpproxy模块进行测试。
1
2
3
4
|
#!define WITH_NAT
modparam("rtpproxy", "rtpproxy_sock", "udp:172.16.4.111:3333")
...
|
其他的参数脚本使用kamailio的默认值, 软电话1004和1007注册到kamailio,使用软电话1004拨打1007。
通话正常有声音.
测试结果
- rtpproxy的日志为:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
DBUG:GLOBAL:rtpp_command_split:375: received command "79_4 Uc8,0,101 ed5ddc640f9144d389f392bd2b6b8501 172.16.80.13 4004 84a153e3091f4204a53f0dc5180c3668;1"
INFO:GLOBAL:rtpp_command_ul_handle:527: new IPv4/IPv4 session ed5ddc640f9144d389f392bd2b6b8501, tag 84a153e3091f4204a53f0dc5180c3668;1 requested, type strong
INFO:ed5ddc640f9144d389f392bd2b6b8501:rtpp_command_ul_handle:592: new session on IPv4 port 40074 created, tag 84a153e3091f4204a53f0dc5180c3668;1
INFO:ed5ddc640f9144d389f392bd2b6b8501:rtpp_stream_prefill_addr:862: pre-filling caller's RTP address with 172.16.80.13:4004
INFO:ed5ddc640f9144d389f392bd2b6b8501:rtpp_stream_prefill_addr:862: pre-filling caller's RTCP address with 172.16.80.13:4005
DBUG:GLOBAL:rtpc_reply_deliver:136: sending reply "79_4 40074\n"
DBUG:GLOBAL:rtpp_command_split:375: received command "73_4 Lc8,0,101 ed5ddc640f9144d389f392bd2b6b8501 172.16.80.13 58192 84a153e3091f4204a53f0dc5180c3668;1 867be556;1"
INFO:ed5ddc640f9144d389f392bd2b6b8501:rtpp_command_ul_handle:517: lookup on ports 40074/40038, session timer restarted
INFO:ed5ddc640f9144d389f392bd2b6b8501:rtpp_stream_prefill_addr:862: pre-filling callee's RTP address with 172.16.80.13:58192
INFO:ed5ddc640f9144d389f392bd2b6b8501:rtpp_stream_prefill_addr:862: pre-filling callee's RTCP address with 172.16.80.13:58193
DBUG:GLOBAL:rtpc_reply_deliver:136: sending reply "73_4 40038\n"
INFO:ed5ddc640f9144d389f392bd2b6b8501:_rtpp_stream_latch:652: caller's address latched in: 172.16.80.13:4005 (RTCP), SSRC=UNKNOWN, Seq=UNKNOWN
INFO:ed5ddc640f9144d389f392bd2b6b8501:_rtpp_stream_latch:652: caller's address latched in: 172.16.80.13:4004 (RTP), SSRC=0x72120CEB, Seq=20529
INFO:ed5ddc640f9144d389f392bd2b6b8501:_rtpp_stream_latch:652: callee's address latched in: 172.16.80.13:58192 (RTP), SSRC=0xB102C9D7, Seq=4384
|
- rtpproxy的监听端口:
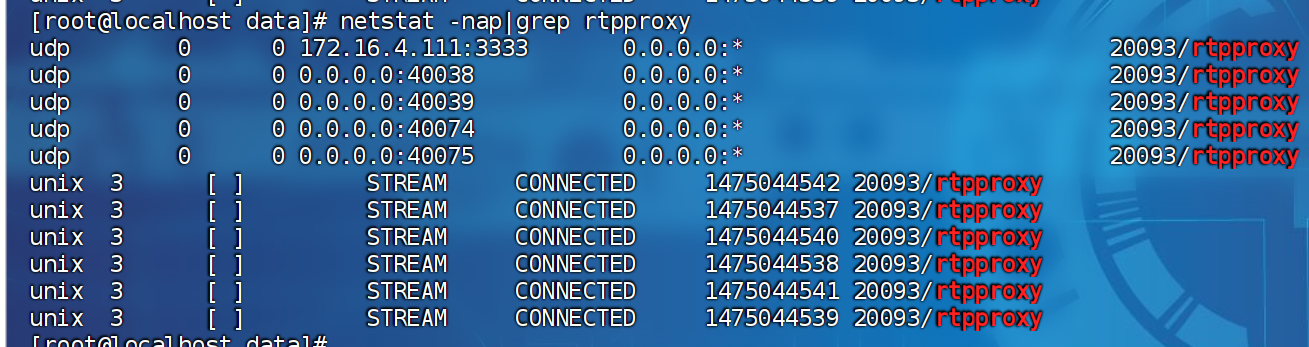
和rtpengine不太一样的是, 如果未主动调用rtpproxy_delete,通话结束后,
其监听的端口不会释放(rtpengine会在没有流的60s后释放端口), rtpproxy会在下一次通话时,释放上次监听的端口。

