背景
mohqueue 模块可以把INVITE请求转移到音乐等待队列中,并播放音乐,直到有接线员接通电话.
官方文档地址: mohqueue。
需要的外部服务为: rtpproxy。
本次测试的版本信息为:
version: kamailio 5.8.5 (x86_64/linux)
参数解析
1
2
3
4
5
6
7
8
9
10
|
# 数据库连接地址
modparam ("mohqueue", "db_url", DB_URL)
# 队列表名
modparam ("mohqueue", "db_qtable", "mohqueues")
# 通话状态表
modparam ("mohqueue", "db_ctable", "mohqcalls")
# 音频文件存放路径
modparam ("mohqueue", "mohdir", "/var/kamailio/MOH")
# 一个队列中最大的通话数,默认:50
modparam ("mohqueue", "moh_maxcalls", 200)
|
本模块需要使用两个数据表:mohqueues和mohqcalls。
重要函数
mohq_process()
检查当前的SIP消息是否涉及队列,如果涉及,则处理此消息并返回true.
mohq_send(queue_name)
将当前的请求发送到不匹配的URI队列中
mohq_retrieve(queue_name, URI)
检索队列中最旧的呼叫,并将其重定向到URI。
mohq_count (queue_name, pvar)
获取队列中的通话数,并将结果存储在pvar中.
实战
配置示例
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
|
loadmodule "rtpproxy.so"
modparam("rtpproxy", "rtpproxy_sock", "udp:172.16.4.111:3333")
modparam("rtpproxy", "rtpproxy_disable_tout", 20)
loadmodule "mohqueue.so"
modparam("mohqueue", "db_url", DBURL)
modparam("mohqueue", "db_qtable", "mohqueues")
modparam("mohqueue", "db_ctable", "mohqcalls")
modparam("mohqueue", "mohdir", "/var/kamailio/MOH")
modparam("mohqueue", "moh_maxcalls", 200)
request_route {
...
if (is_method("INVITE")) {
mohq_count("abc", "$var(mohqcnt)");
xlog("L_INFO", "abc queue has $var(mohqcnt) calls!\n");
if (mohq_process()) {
xlog("L_INFO", "process done\n");
} else {
xlog("L_INFO", "mohq_process error\n");
}
}
...
}
|
- 数据表:
mohqueues插入数据:
1
|
insert into mohqueues (`name`, `uri`,`mohdir`,`moh_file`,`debug`) values ('abc', 'sip:1008@172.16.4.111:5461','/var/kamailio/MOH','test.pcm', 1);
|
uri很重要, 要和Request-URI保持一致,不然会无法触发mohq_process
- 上传音频文件到
/var/kamailio/MOH/目录下
1
2
3
|
ll /var/kamailio/MOH/
total 540
-rwxrwxrwx. 1 root root 550080 Jul 28 13:53 test.pcm.8
|
需要注意的是:
音频文件的名称比mohqueues表中的moh_file字段的值多了’.type'
-
如果kamailio和rtpproxy使用两个容器部署, 那么rtpproxy也要有/var/kamailio/MOH目录和相关的文件.
-
rtpproxy的运行命令为:
1
|
rtpproxy -l 0.0.0.0 -L 4096 -m 40000 -M 40100 -s udp:172.16.4.111:3333 -d DBUG -f -F
|
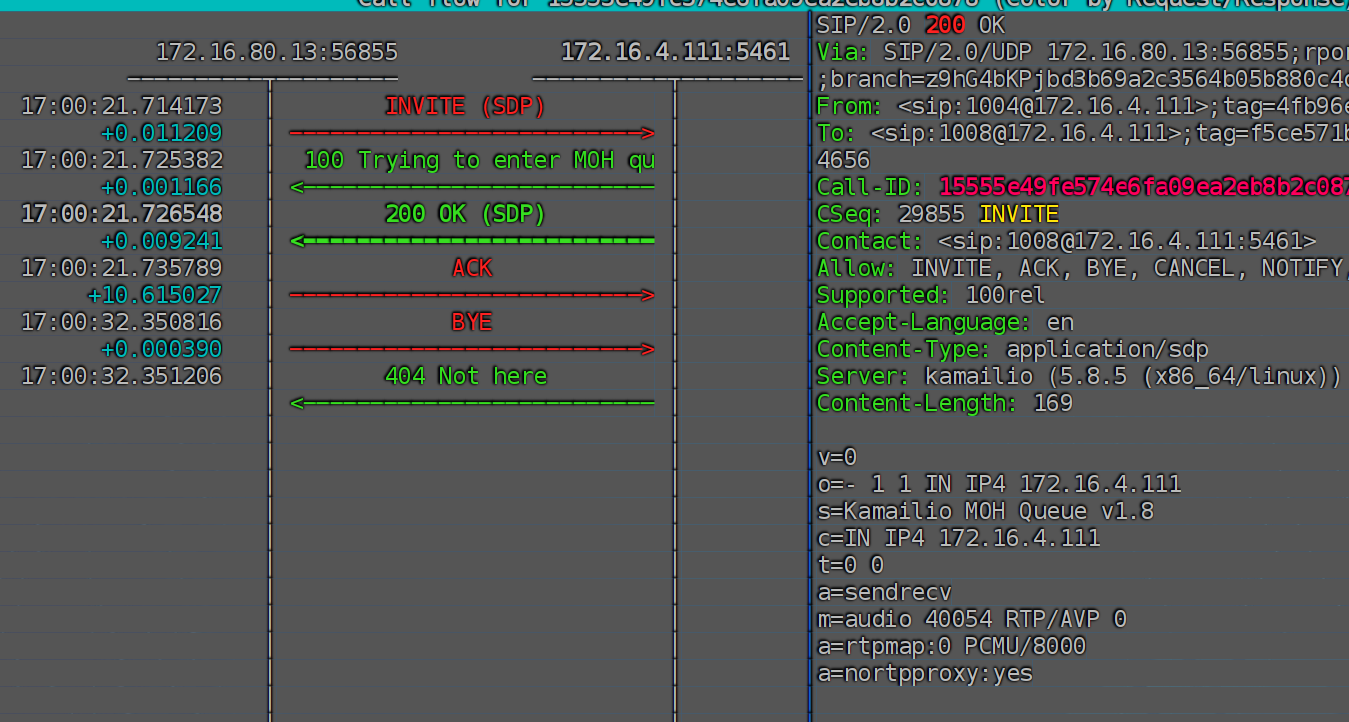
测试
使用软电话拨打1008, 可以听到录音文件的内容,但是有滋滋啦啦的声音,应该是音频格式问题,具体的格式需要后续再排查。
kamailio的日志为:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
14(10568) INFO: <script>: ------172.16.80.13:52570|172.16.4.111:5461|udp|INVITE
14(10568) INFO: <script>: abc queue has 0 calls!
14(10568) DEBUG: mohqueue [mohq_funcs.c:2554]: mohq_debug(): create_call: Added call (<sip:1004@172.16.4.111>;tag=6960f3996dc741dba443fef5900f3f05) to queue (abc)
14(10568) DEBUG: mohqueue [mohq_funcs.c:2554]: mohq_debug(): mohq_process: Processing INVITE, queue (abc)
14(10568) DEBUG: mohqueue [mohq_funcs.c:2554]: mohq_debug(): first_invite_msg: Making offer for RTP link for call (<sip:1004@172.16.4.111>;tag=6960f3996dc741dba443fef5900f3f05) from queue (abc)
14(10568) DEBUG: mohqueue [mohq_funcs.c:2554]: mohq_debug(): send_rtp_answer: Answering RTP link for call (<sip:1004@172.16.4.111>;tag=6960f3996dc741dba443fef5900f3f05)
14(10568) DEBUG: mohqueue [mohq_funcs.c:2554]: mohq_debug(): start_stream: Starting RTP link for call (<sip:1004@172.16.4.111>;tag=6960f3996dc741dba443fef5900f3f05)
14(10568) ERROR: dialog [dlg_handlers.c:542]: dlg_onreply(): Faked reply!
14(10568) DEBUG: mohqueue [mohq_funcs.c:2554]: mohq_debug(): send_rtp_answer: Responded to INVITE with RTP for call (<sip:1004@172.16.4.111>;tag=6960f3996dc741dba443fef5900f3f05)
14(10568) INFO: <script>: process done
15(10569) INFO: <script>: ------172.16.80.13:52570|172.16.4.111:5461|udp|ACK
16(10570) INFO: <script>: ------172.16.80.13:52570|172.16.4.111:5461|udp|BYE
34(10588) ERROR: mohqueue [mohq_funcs.c:1348]: invite_cb(): invite_cb: INVITE failed for call (<sip:1004@172.16.4.111>;tag=6960f3996dc741dba443fef5900f3f05), code=20000, callstate=68!
34(10588) DEBUG: mohqueue [mohq_funcs.c:2554]: mohq_debug(): delete_call: Deleting call (<sip:1004@172.16.4.111>;tag=6960f3996dc741dba443fef5900f3f05) from queue (abc)
|
rtpproxy的日志为:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
DBUG:GLOBAL:rtpp_command_split:375: received command "10568_4 Uc8,0,101 0251ec9fbe4548c1a8dda6e69e8b91a4 172.16.80.13 4008 6960f3996dc741dba443fef5900f3f05;1"
INFO:GLOBAL:rtpp_command_ul_handle:527: new IPv4/IPv4 session 0251ec9fbe4548c1a8dda6e69e8b91a4, tag 6960f3996dc741dba443fef5900f3f05;1 requested, type strong
INFO:0251ec9fbe4548c1a8dda6e69e8b91a4:rtpp_command_ul_handle:592: new session on IPv4 port 40072 created, tag 6960f3996dc741dba443fef5900f3f05;1
INFO:0251ec9fbe4548c1a8dda6e69e8b91a4:rtpp_stream_prefill_addr:862: pre-filling caller's RTP address with 172.16.80.13:4008
INFO:0251ec9fbe4548c1a8dda6e69e8b91a4:rtpp_stream_prefill_addr:862: pre-filling caller's RTCP address with 172.16.80.13:4009
DBUG:GLOBAL:rtpc_reply_deliver:136: sending reply "10568_4 40072\n"
DBUG:GLOBAL:rtpp_command_split:375: received command "10568_5 LZ20c8 0251ec9fbe4548c1a8dda6e69e8b91a4 172.16.80.13 1 6960f3996dc741dba443fef5900f3f05;1 f5ce571b08e47ce350df4b28201d4d1c-1b725a54;1"
INFO:0251ec9fbe4548c1a8dda6e69e8b91a4:rtpp_command_ul_handle:517: lookup on ports 40072/40084, session timer restarted
INFO:0251ec9fbe4548c1a8dda6e69e8b91a4:rtpp_stream_prefill_addr:862: pre-filling callee's RTP address with 172.16.80.13:1
INFO:0251ec9fbe4548c1a8dda6e69e8b91a4:rtpp_stream_prefill_addr:862: pre-filling callee's RTCP address with 172.16.80.13:2
INFO:0251ec9fbe4548c1a8dda6e69e8b91a4:rtpp_command_ul_handle:663: RTP packets from callee will be resized to 20 milliseconds
DBUG:GLOBAL:rtpc_reply_deliver:136: sending reply "10568_5 40084\n"
DBUG:GLOBAL:rtpp_command_split:375: received command "10568_6 P-1 0251ec9fbe4548c1a8dda6e69e8b91a4 /var/kamailio/MOH/test.pcm session 6960f3996dc741dba443fef5900f3f05;1 f5ce571b08e47ce350df4b28201d4d1c-1b725a54;1"
INFO:0251ec9fbe4548c1a8dda6e69e8b91a4:rtpp_stream_handle_play:511: -1 times playing prompt /var/kamailio/MOH/test.pcm codec 8: SSRC=0xAA2B056D, seq=26343
DBUG:GLOBAL:rtpc_reply_deliver:136: sending reply "10568_6 0\n"
INFO:0251ec9fbe4548c1a8dda6e69e8b91a4:_rtpp_stream_latch:652: caller's address latched in: 172.16.80.13:4009 (RTCP), SSRC=UNKNOWN, Seq=UNKNOWN
INFO:0251ec9fbe4548c1a8dda6e69e8b91a4:_rtpp_stream_latch:652: caller's address latched in: 172.16.80.13:4008 (RTP), SSRC=0x24982D1B, Seq=14344
|
相关的sip信令为: